![]()
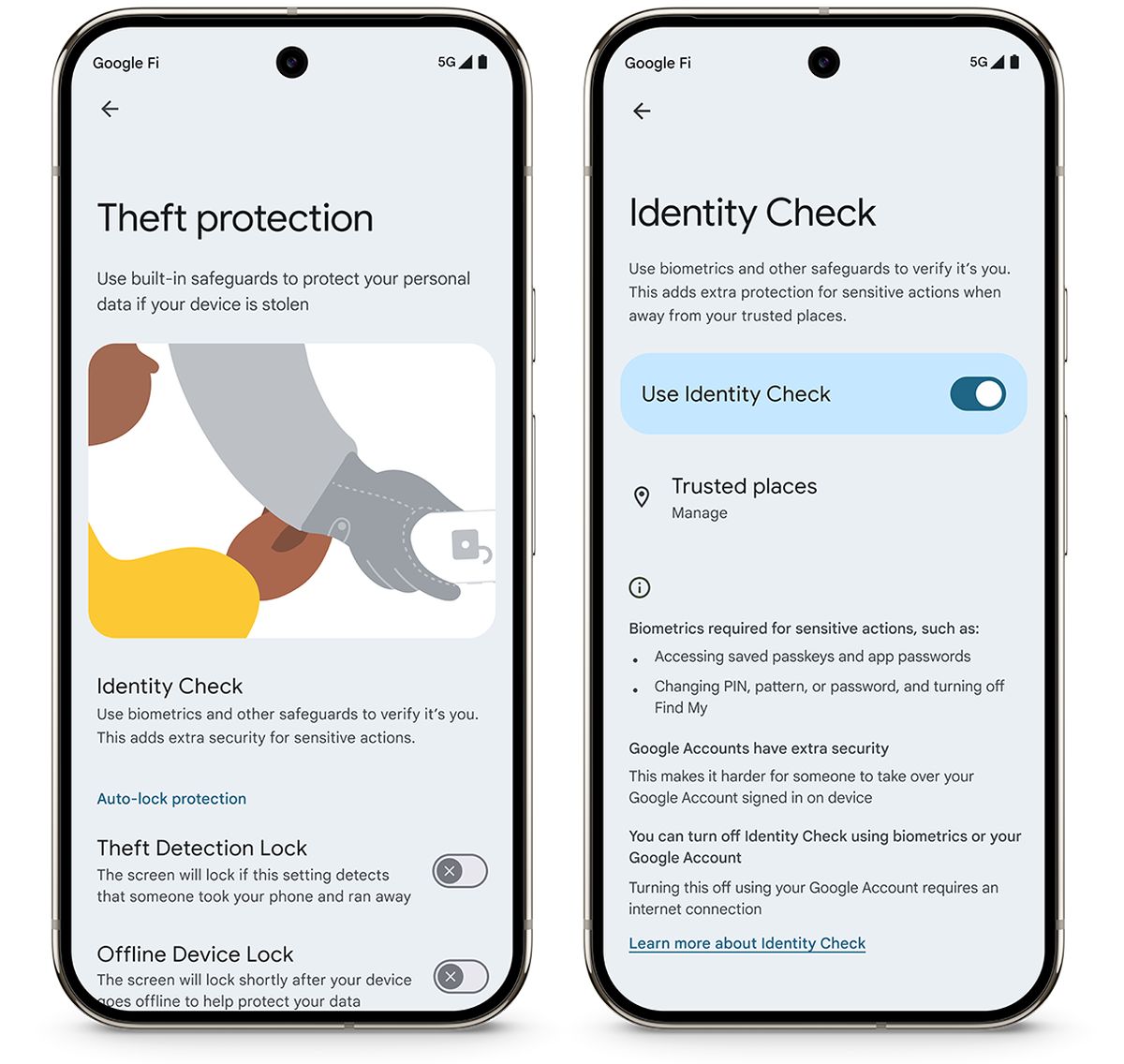
Google has introduced a new security feature called Identity Check for supported Android devices, designed to lock sensitive settings behind biometric authentication when users are outside of trusted locations.
Google introduces identity check to enhance Android security
When activated, Identity Check mandates explicit biometric authentication for specific actions when the device is not in an approved area. These actions include:
- Accessing saved passwords and passkeys with Google Password Manager
- Autofilling passwords in apps from Google Password Manager, except in Chrome
- Changing screen lock options, such as PIN, pattern, and password
- Altering biometrics like Fingerprint or Face Unlock
- Running a factory reset
- Turning off Find My Device
- Disabling any theft protection features
- Viewing trusted places
- Turning off Identity Check
- Setting up a new device with the current one
- Adding or removing a Google Account
- Accessing Developer options
Identity Check also enhances the protection of Google Accounts, thwarting unauthorized access to any Google Account signed in on the device.
Pixel update: Google removes globe icon in Android 15 QPR2 Beta 3
This feature is currently available exclusively for Google Pixel phones running Android 15 and select Samsung Galaxy devices operating on One UI 7. Users can enable it by navigating to Settings > Google > All services > Theft protection > Identity Check.
This announcement aligns with Google’s ongoing strategy to bolster device security against theft, which also includes features like Theft Detection Lock, Offline Device Lock, and Remote Lock. Recently, Google announced the global rollout of its AI-powered Theft Detection Lock to all Android devices running Android 10 and later.
Furthermore, Google is collaborating with the GSMA and industry experts to combat mobile device theft, sharing information and tools for prevention.
In a related development, Google launched the Chrome Web Store for Enterprises, allowing organizations to curate a list of extensions that can be safely installed on employees’ browsers, minimizing the risk of users installing harmful or unverified add-ons.
Recently, a spear-phishing campaign targeted Chrome extension developers, leading to the insertion of malicious code intended to harvest sensitive data, including API keys and session cookies from significant platforms like ChatGPT and Facebook for Business. This supply chain attack has reportedly been active since December 2024, according to analysis from French cybersecurity firm Sekoia.
Sekoia described the threat actor as persistent, noting that by late November 2024, the attacker shifted tactics from distributing their own malicious Chrome extensions via fake websites to compromising legitimate extensions through phishing emails, malicious OAuth applications, and code injections into already compromised extensions.
Featured image credit: Google






