
The macOS Ferret family, known for being used by North Korean APTs for cyber espionage, has introduced a new variant named Flexible-Ferret that is currently evading detection measures implemented by Apple.
Flexible-Ferret malware variant evades Apple’s XProtect measures
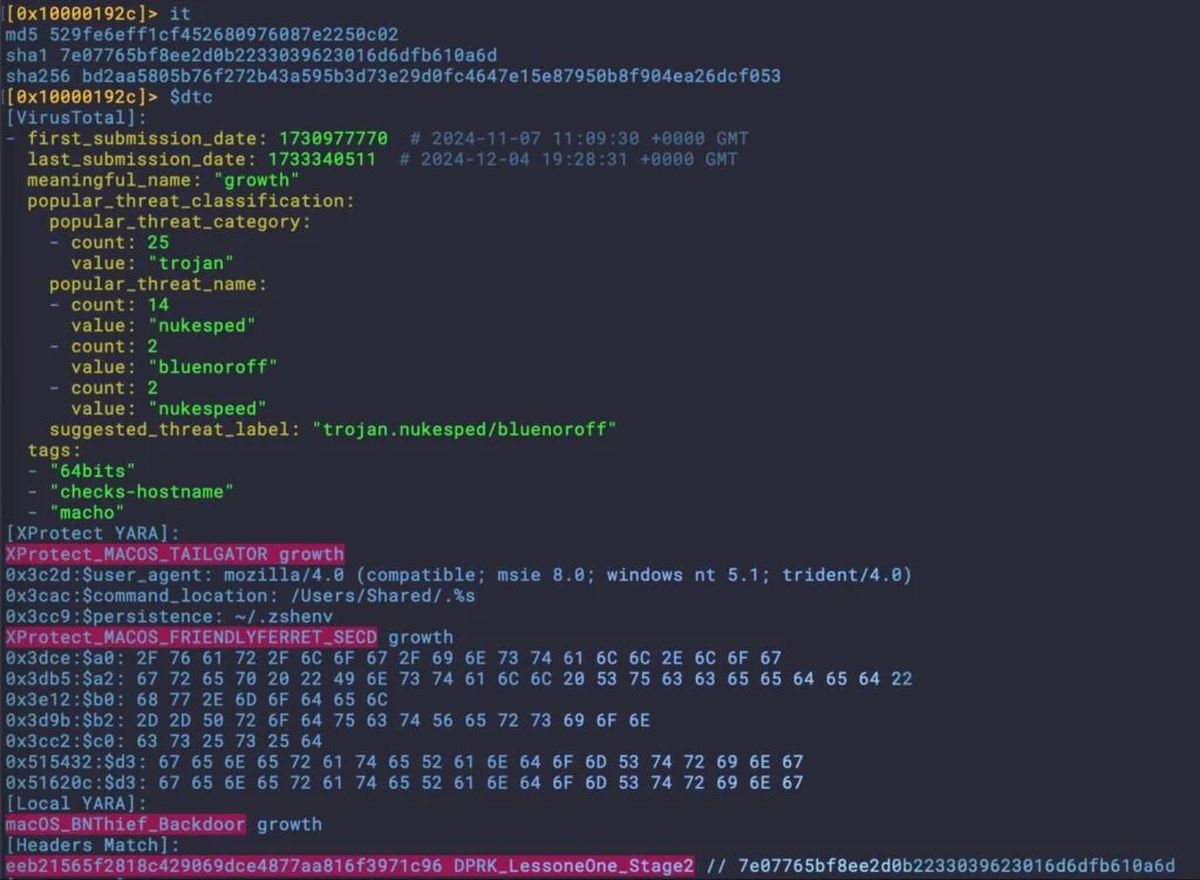
This detection-resistant variant was identified by researchers at SentinelOne, who noted its ability to bypass the recent XProtect signature update intended to block Ferret infections. Unlike its predecessors, Flexible-Ferret carries a legitimate Apple Developer signature and Team ID, which adds a layer of deception to its operation.
The Ferret malware family is associated with the “Contagious Interview” campaign, where threat actors trick victims into installing malware by posing as job interviewers. This campaign reportedly began in November 2023 and has involved multiple malware variants such as FROSTYFERRET_UI, FRIENDLYFERRET_SECD, and MULTI_FROSTYFERRET_CMDCODES—all of which were covered in Apple’s most recent XProtect update.
Flexible-Ferret evades XProtect
SentinelOne’s analysis revealed that under XProtect version 5286, the new Flexible-Ferret variant went undetected. Through ongoing examination, they discovered a ChromeUpdate variant known as Mac-Installer.InstallerAlert, which is also signed with a valid Apple Developer ID and Team ID, thereby maintaining its connection to the existing FERRET family.
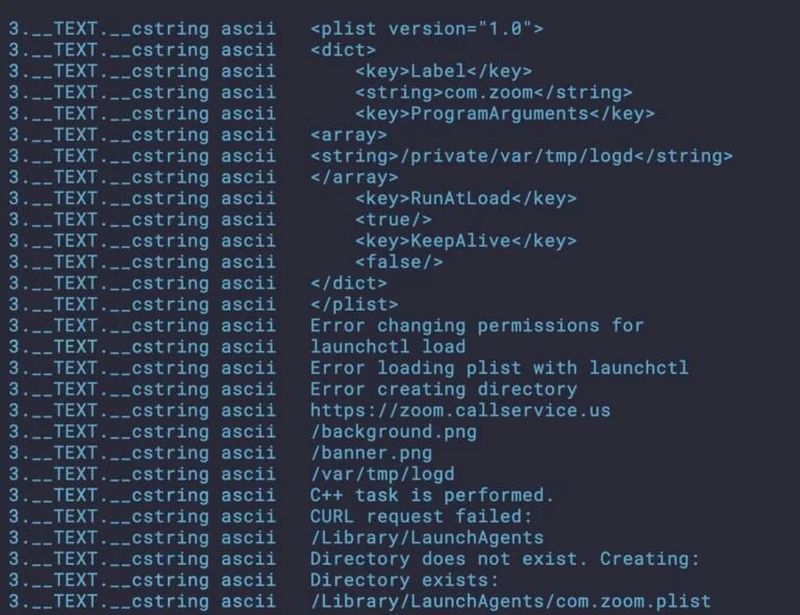
The malware dropper, termed versus.pkg, contains two applications—InstallerAlert.app and versus.app—and a standalone binary named “zoom.” When executed, the “zoom” binary connects to a suspicious domain unrelated to Zoom services and elevates system privileges. Simultaneously, InstallerAlert.app generates an error message that mimics macOS Gatekeeper warnings while deploying a persistence agent.
Despite sharing 86% code similarity with the ChromeUpdate, the Mac-Installer was not flagged by XProtect until it was linked to a revoked Developer ID, which allowed researchers to uncover further Flexible-Ferret samples.
According to SentinelOne, the “Contagious Interview” campaign exemplifies ongoing, active threat actor maneuvers where adversaries adapt signed applications into functionally similar unsigned versions to evade security measures. This includes diverse tactics aimed at a broad range of targets within the developer community, facilitated through social media and code-sharing sites such as GitHub.
Researchers pointed out that threat actor groups focused on macOS include prominent entities from North Korea, China, and Russia. Boris Cipot, a senior security engineer at Black Duck, emphasized the continuous evolution of techniques to bypass security defenses.
Apple’s recent signature update targeted several components of this malware family, including a backdoor disguised as an operating system file named com.apple.secd, in addition to the ChromeUpdate and CameraAccess persistence modules. Notably, components in the FERRET malware family exhibit commonalities with others associated with DPRK campaigns, including file sharing through Dropbox and IP resolution via api.ipify.org.
Featured image credit: Wesson Wang/Unsplash






